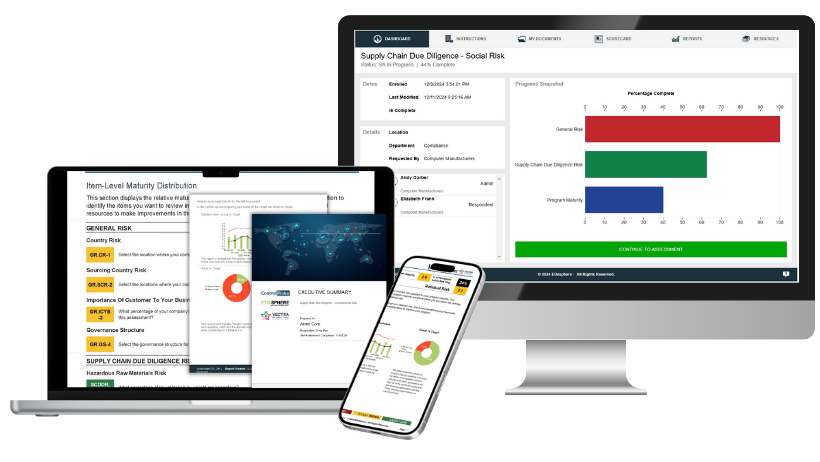
Supply Chain Risk Management Solution
For companies with thousands of suppliers, we make risk identification manageable, leveraging a data-driven funnel and deep supply chain expertise to identify your highest risks and providing in-depth analysis and quantifiable risk ratings. Our solution not only assesses controls but quantifies residual risk, equipping you with prioritized action items and scalable remediation strategies.
Real Stories, Real Supply ChainConfidence
We deliver an end-to-end understanding of risk across your supply chain. By combining modern-technology and human expertise we enable you to improve supplier intelligence – through expert insights into inherent environmental and social risk plus a roadmap to reduce residual risk.
Discover how leading companies empower their supply chains to navigate evolving regulations and exceed customer expectations. Hear their stories and see how they achieve success with help from Ethisphere.

Be part of the largest gathering of ethics and compliance professionals. The Global Ethics summit unites industry leaders to advance ethical culture. Gain actionable insights, practical tools, and peer connections to strengthen your program and drive integrity in your business.
The Challenges Facing Supply Chains
Customer and regulatory pressures, and geopolitical events, combined with increasing due diligence regulations are putting increased pressure on supply chains, as well as procurement and compliance teams.
Meeting and exceeding supply chain due diligence requirements necessitates a scalable, risk-based process for identifying, managing and mitigating supplier residual risk.
With one solution and world-leading experts at your side, your organization will identify supplier vulnerabilities and receive expert analysis, actionable recommendations, and an action plan to mitigate risks—helping your supply chain meet growing regulations and increasing customer pressure.
________________________
Stay ahead of evolving regulations with our new Supply Chain Due Diligence: Regulations & Guidance Comparison Guide covering the areas and issues that need to be addressed when conducting supply chain due diligence across multiple regulatory environments.
Identify high risk suppliers
- Screen and prioritize suppliers with a customized risk-based process built for your supply chain
- Incumbent suppliers prioritised for enhanced risk assessment
- Automated prioritisation and due diligence for new suppliers
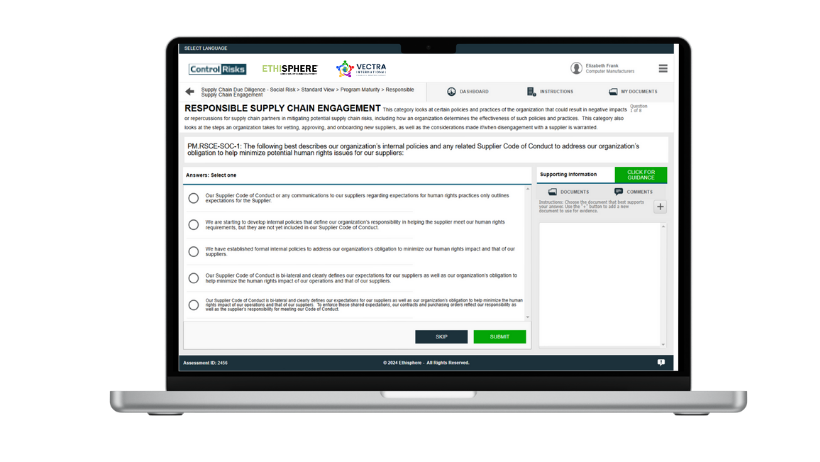
Lack of insight into individual supplier practices
- Assess the strength of your suppliers’ due diligence policies, systems and controls to ensure regulatory alignment
- Receive a detailed maturity assessment of supplier due diligence systems and controls
- Ensure potential or actual supplier ESG controversies are-identified, managed and remediated
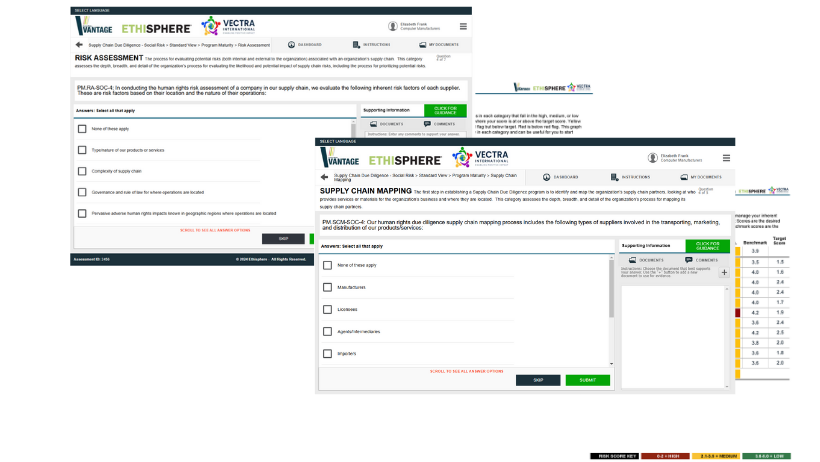
Inadequate data and insight into inherent and residual supplier risks
- Receive expert analysis on supplier risk performance trends with corresponding recommendations to senior management
- Receive residual risk report and supplier red-flag findings
- Benchmark supplier maturity against peers and own entity performance

Aligning with evolving regulatory compliance risks
- Assessments mapped to EU and Global Supply Chain Due Diligence Regulations
- Insight into issues relevant from reputational, regulatory, operational and security standpoints for over 100 countries
Learn how the 2024 World’s Most Ethical Companies®
manage their supply chains
84%
Reevaluate third-party risk ranking on an ongoing basis or annually.
55%
Conduct due diligence before entering into all 3rd party relationships.
85%
Have audited high-risk 3rd parties in the last 2 years.









Hear From Leaders Who Trust BELA
“How we allocate and spend our time and resources across the work we assign to our people within the Ethics and Compliance team is very important. The Ethisphere team and assessments allow us to, in a very measured, precise way, allocate our resources and our time to really get the best bang for our buck.”
– Antonio Fernandez, VP, Chief Compliance Officer FirstEnergy
At Ethisphere, we empower companies to succeed
by turning ethics and compliance into a competitive advantage.
We help identify what a strong program looks like—based on regulatory guidance, best practices, and peer insights. With access to unmatched data, a like-minded community, and proven resources, we make it easy to understand your program, prioritize actions, and map out an improvement plan. Our community connects you with top practitioners and experts, offering the tools to build trust, reduce risk, and drive long-term success. Ethisphere gives you everything you need to elevate your ethics and compliance into a key driver of business success.